How To Use RemoteIoT Behind Firewall Using Mac Server: A Comprehensive Guide
Imagine this: You're trying to access your IoT devices from afar, but your network is locked down by a firewall. Sound familiar? Don’t worry, you’re not alone. Many tech enthusiasts and professionals face this challenge daily. Using RemoteIoT behind a firewall with a Mac server is not only possible but can be a game-changer for your setup. In this guide, we’ll walk you through everything you need to know to make it happen.
Firewalls are like the bouncers at a club—they decide who gets in and who stays out. While they’re essential for security, they can sometimes block legitimate connections, especially when you’re dealing with IoT devices. If you’re running a Mac server, you have a powerful tool at your disposal to bypass these restrictions without compromising safety. Let’s dive in and explore how you can make it work.
This guide isn’t just about theory; it’s about practical solutions that you can implement right away. Whether you’re a beginner or an advanced user, we’ve got you covered. From setting up your Mac server to configuring firewalls and ensuring secure connections, we’ll cover it all. So grab a coffee, sit back, and let’s get started!
Read also:Trippie Redd Leaked Tapes The Untold Story Behind The Hype
Understanding RemoteIoT and Its Role in Network Management
Before we jump into the nitty-gritty, let’s talk about what RemoteIoT actually is. RemoteIoT refers to the ability to control and manage IoT devices remotely. These devices can range from smart home gadgets to industrial sensors, and they all rely on stable and secure connections to function properly. When you’re behind a firewall, however, things can get tricky.
Using a Mac server as the backbone of your RemoteIoT setup can provide several advantages. First, macOS is known for its robust security features, which makes it an excellent choice for managing sensitive data. Second, its compatibility with various networking protocols ensures smooth communication with your IoT devices.
Here are some key benefits of using RemoteIoT:
- Centralized control over all your IoT devices
- Enhanced security through encrypted connections
- Improved efficiency in managing network resources
- Scalability to accommodate growing device fleets
Setting Up Your Mac Server for RemoteIoT
Step 1: Preparing Your Mac
Before you can use your Mac as a server, you’ll need to ensure it’s properly configured. Start by installing macOS Server, which is available for free from the App Store. This app transforms your Mac into a powerful server capable of handling multiple tasks, including remote access and network management.
Once installed, open the Server app and follow the setup wizard. You’ll be prompted to choose which services you want to enable. For RemoteIoT, focus on enabling the following:
- File Sharing
- Remote Access (SSH)
- Web
Step 2: Configuring Network Settings
Your Mac server needs to be on the same network as your IoT devices to function effectively. Make sure your Wi-Fi or Ethernet connection is stable and that your router supports the necessary protocols. Additionally, assign a static IP address to your Mac to ensure consistent connectivity.
Read also:Peter Dinklage Wife The Love Story Behind The Game Of Thrones Legend
To do this, go to System Preferences > Network, select your connection type, and click Advanced. From there, you can manually set an IP address that won’t change, even if your network restarts.
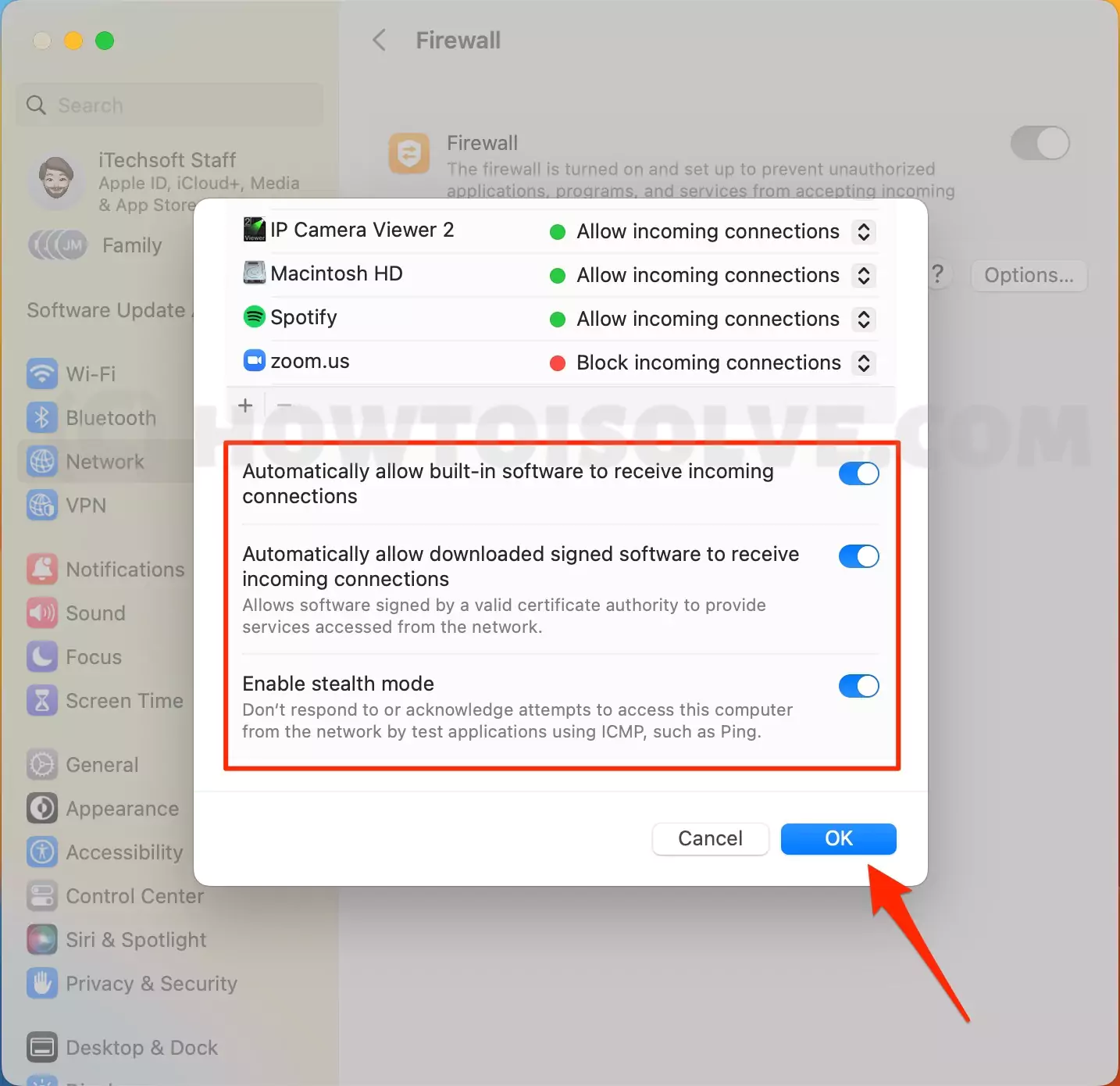
Configuring Your Firewall for RemoteIoT
Step 1: Identifying Open Ports
Firewalls work by blocking unauthorized traffic based on predefined rules. To allow RemoteIoT to function, you’ll need to open specific ports on your firewall. Common ports used for IoT communication include:
- Port 22 for SSH
- Port 80 for HTTP
- Port 443 for HTTPS
You can check which ports are open on your network using tools like Nmap or by consulting your router’s settings page. If any of these ports are closed, you’ll need to configure your firewall to allow them.
Step 2: Creating Firewall Rules
Most modern firewalls allow you to create custom rules to permit specific types of traffic. Log in to your router’s admin panel and navigate to the firewall settings. From there, add a new rule that allows traffic on the ports you identified earlier.
Be sure to specify the source and destination IP addresses to minimize security risks. For example, you might allow traffic only from your Mac server’s IP address to ensure that only authorized devices can connect.
Securing Your RemoteIoT Setup
Security should always be a top priority when working with IoT devices. Here are some best practices to keep your setup safe:
- Use strong, unique passwords for all accounts
- Enable two-factor authentication (2FA) whenever possible
- Regularly update your software and firmware
- Monitor your network for suspicious activity
macOS comes with built-in security features like FileVault and Gatekeeper, which can help protect your data. Additionally, consider using a Virtual Private Network (VPN) to encrypt your communications and further enhance security.
Troubleshooting Common Issues
Problem 1: Connection Timeout
If you’re experiencing connection timeouts, it could be due to several factors. Check the following:
- Ensure that your Mac server is online and reachable
- Verify that the necessary ports are open on your firewall
- Test your connection using tools like Ping or Traceroute
Problem 2: Slow Performance
Slow performance can be frustrating, especially when you’re managing multiple devices. To improve speed:
- Optimize your network settings
- Reduce the number of active connections
- Upgrade your hardware if necessary
Best Practices for Managing RemoteIoT
Managing IoT devices remotely requires a strategic approach. Here are some tips to help you stay organized and efficient:
- Create a detailed inventory of all your devices
- Set up automated updates to keep everything current
- Document your configurations for future reference
Additionally, consider using third-party tools like Homebridge or OpenHAB to streamline your management process. These platforms offer user-friendly interfaces and a wide range of integrations to make your life easier.
Case Study: Real-World Application
Let’s look at a real-world example of how RemoteIoT can be used behind a firewall with a Mac server. A small business owner wanted to monitor energy usage across multiple locations without compromising security. By setting up a Mac server and configuring their firewall to allow specific IoT traffic, they were able to achieve their goals while maintaining peace of mind.
The results? A more efficient operation, reduced energy costs, and improved overall security. This case study highlights the potential of RemoteIoT when implemented correctly.
Future Trends in RemoteIoT
The world of IoT is evolving rapidly, and new technologies are emerging all the time. Some trends to watch include:
- Edge computing for faster processing
- AI-driven analytics for smarter decision-making
- 5G networks for enhanced connectivity
As these technologies mature, they’ll open up new possibilities for RemoteIoT users. Staying informed about these developments will help you stay ahead of the curve and make the most of your setup.
Conclusion: Taking Action
Using RemoteIoT behind a firewall with a Mac server may seem daunting at first, but with the right tools and knowledge, it’s entirely achievable. By following the steps outlined in this guide, you can create a secure and efficient system that meets your needs.
Now it’s your turn to take action. Whether you’re setting up your first Mac server or optimizing an existing one, remember to prioritize security and efficiency. And don’t forget to share your experiences in the comments below—we’d love to hear how this guide helped you!
For more tips and tricks on all things tech, be sure to explore our other articles. Happy networking!
Table of Contents
- Understanding RemoteIoT and Its Role in Network Management
- Setting Up Your Mac Server for RemoteIoT
- Configuring Your Firewall for RemoteIoT
- Securing Your RemoteIoT Setup
- Troubleshooting Common Issues
- Best Practices for Managing RemoteIoT
- Case Study: Real-World Application
- Future Trends in RemoteIoT
- Conclusion: Taking Action
Article Recommendations