Access IoT Device Behind Firewall AWS: The Ultimate Guide For Tech Enthusiasts
So, you're here to learn about accessing IoT devices behind a firewall using AWS. Let's be honest, this is one of those tech topics that can make your head spin if you don’t break it down properly. But don’t worry, we’ve got your back. Whether you’re a seasoned developer or just starting out, understanding how to access IoT devices securely is crucial in today’s connected world.
Picture this: you’ve got all these amazing IoT devices, but they’re locked behind a corporate firewall. It’s like trying to get into an exclusive club without the VIP pass. That’s where AWS comes in. AWS offers a range of tools and services that can help you connect to these devices without compromising security. We’ll dive deep into this in a bit.
Before we jump into the nitty-gritty, let’s talk about why this is important. IoT is growing at an insane pace, and with that growth comes challenges. Security is one of the biggest concerns, and firewalls are there to protect your network. But what happens when you need to access those devices from the outside? That’s where our guide comes in handy.
Read also:Aisha Sofey Leaks Unveiling The Truth Behind The Controversy
Understanding AWS IoT and Firewalls
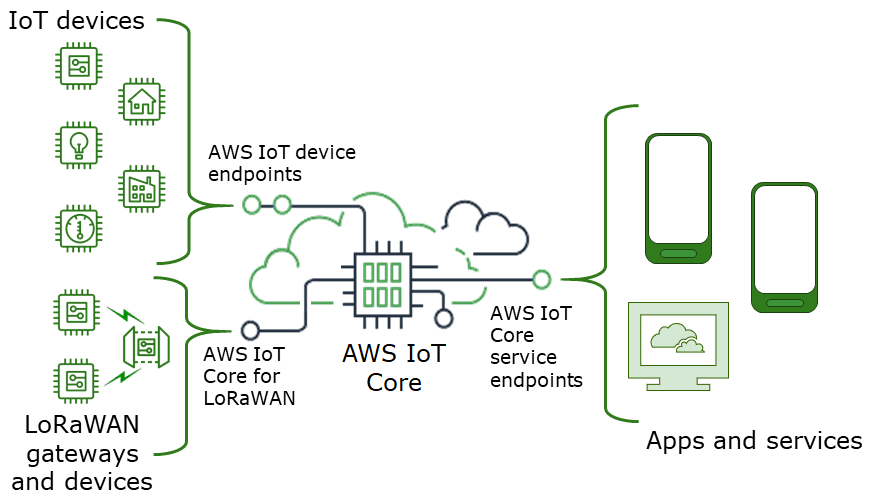
Alright, let’s start by breaking down what AWS IoT is all about. AWS IoT Core is basically the heart of AWS’s IoT ecosystem. It allows you to connect, monitor, and interact with billions of devices. But here’s the thing—when those devices are behind a firewall, things can get tricky.
A firewall is like a bouncer at a club. It decides who gets in and who doesn’t. In the digital world, it protects your network from unauthorized access. But sometimes, you need to let certain devices or services in. That’s where AWS comes in with its suite of tools to help you manage this delicate balance.
Key Features of AWS IoT
Let’s look at some of the key features that make AWS IoT so powerful:
- Device Gateway: This is like the front door to your IoT devices. It handles secure communication between devices and AWS.
- Rules Engine: Think of it as the brains of the operation. It helps you route data from devices to other AWS services.
- Device Shadow: This allows you to keep track of device state, even when the device is offline.
These features make AWS IoT a game-changer when it comes to managing IoT devices, especially those behind firewalls.
Why Accessing IoT Devices Behind Firewalls is a Challenge
Now, let’s talk about the elephant in the room—why is accessing IoT devices behind firewalls such a big deal? Well, it all comes down to security. Firewalls are there to protect your network from malicious actors. But when you need to access devices from the outside, you have to find a way to do it securely.
There are a few common challenges:
Read also:Tulsi Gabbard Parents The Unsung Pillars Behind A Political Phenomenon
- Network Restrictions: Firewalls often block incoming connections, making it difficult to access devices directly.
- Security Concerns: Opening up your network to external access can pose significant security risks.
- Complexity: Setting up secure access can be a complex process, especially for those new to AWS.
But don’t worry, AWS has solutions for all these challenges. We’ll explore them in the next section.
Solutions for Accessing IoT Devices Behind Firewalls
So, how do you actually access IoT devices behind firewalls using AWS? There are a few different approaches you can take:
1. Using AWS IoT Core with MQTT over WebSocket
One of the most popular methods is using MQTT over WebSocket. This allows you to establish a secure connection to your devices without needing to open up your firewall. Here’s how it works:
- Devices connect to AWS IoT Core using WebSocket.
- The connection is encrypted using TLS, ensuring secure communication.
- You can then interact with your devices through the AWS IoT console or API.
This method is great because it doesn’t require any changes to your firewall configuration.
2. Setting Up a VPC Endpoint
Another option is to set up a VPC (Virtual Private Cloud) endpoint. This allows your devices to communicate with AWS IoT Core without going through the public internet. Here’s what you need to do:
- Create a VPC endpoint for AWS IoT Core.
- Configure your devices to use the VPC endpoint.
- Update your firewall rules to allow traffic to the VPC endpoint.
This method is ideal for organizations that want to keep their network traffic internal.
3. Using AWS IoT Greengrass
AWS IoT Greengrass is another powerful tool that can help you manage IoT devices behind firewalls. It allows you to run local compute, messaging, and data caching for connected devices. Here’s how it can help:
- Devices can communicate with each other locally, without needing to go through the firewall.
- Data can be processed locally, reducing the need for external access.
- Greengrass can act as a bridge between local devices and AWS IoT Core.
This method is perfect for scenarios where you need to process data locally but still want to leverage AWS’s cloud capabilities.
Best Practices for Secure Access
Now that we’ve covered some of the methods for accessing IoT devices behind firewalls, let’s talk about best practices for ensuring secure access:
- Use Strong Authentication: Always use strong authentication mechanisms, such as certificates or tokens, to secure your devices.
- Encrypt All Communication: Ensure all communication between devices and AWS is encrypted using TLS.
- Regularly Update Firmware: Keep your devices’ firmware up to date to protect against vulnerabilities.
By following these best practices, you can ensure that your IoT devices are accessed securely, even behind a firewall.
Data Security and Compliance
When it comes to accessing IoT devices behind firewalls, data security and compliance are critical. Here are a few things to keep in mind:
- Compliance Standards: Make sure you’re compliant with relevant standards, such as GDPR or HIPAA, depending on your industry.
- Data Encryption: Encrypt all data both in transit and at rest to protect sensitive information.
- Access Controls: Implement strict access controls to ensure only authorized personnel can access your devices.
By prioritizing data security and compliance, you can protect your organization and its customers.
Real-World Examples
Let’s look at a couple of real-world examples of how organizations are using AWS to access IoT devices behind firewalls:
Example 1: Smart Manufacturing
A manufacturing company uses AWS IoT to monitor and manage its production line. All the sensors and machines are behind a firewall, but the company uses MQTT over WebSocket to securely access them. This allows them to monitor production in real-time and make data-driven decisions.
Example 2: Smart Healthcare
A healthcare provider uses AWS IoT Greengrass to manage medical devices in its hospitals. The devices communicate locally, reducing the need for external access. However, when external access is needed, the provider uses a VPC endpoint to ensure secure communication.
These examples demonstrate the versatility of AWS IoT in different industries.
Troubleshooting Common Issues
Even with the best-laid plans, things can go wrong. Here are some common issues you might encounter and how to troubleshoot them:
- Connection Issues: If you’re having trouble connecting to your devices, check your firewall rules and ensure that the necessary ports are open.
- Authentication Errors: If you’re getting authentication errors, verify that your certificates or tokens are valid and properly configured.
- Performance Problems: If you’re experiencing performance issues, consider optimizing your network configuration or using AWS IoT Greengrass for local processing.
By addressing these issues promptly, you can ensure smooth operation of your IoT devices.
Future Trends in IoT and Firewall Management
As IoT continues to evolve, so do the methods for managing devices behind firewalls. Here are a few trends to watch:
- Edge Computing: More processing will happen at the edge, reducing the need for external access.
- Zero Trust Architecture: Organizations will adopt zero trust principles to enhance security.
- AI and Machine Learning: These technologies will play a bigger role in managing and securing IoT devices.
By staying ahead of these trends, you can future-proof your IoT infrastructure.
Conclusion
In conclusion, accessing IoT devices behind firewalls using AWS is a challenge, but one that can be overcome with the right tools and strategies. Whether you choose MQTT over WebSocket, VPC endpoints, or AWS IoT Greengrass, AWS offers a range of solutions to help you manage your IoT devices securely.
We encourage you to try out these methods and see which one works best for your organization. And don’t forget to follow best practices for secure access and data protection. If you found this guide helpful, feel free to leave a comment or share it with your network. Happy connecting!
Table of Contents
Access IoT Device Behind Firewall AWS: The Ultimate Guide for Tech Enthusiasts
Understanding AWS IoT and Firewalls
Why Accessing IoT Devices Behind Firewalls is a Challenge
Solutions for Accessing IoT Devices Behind Firewalls
Best Practices for Secure Access
Article Recommendations