Mastering SSH Control For IoT Devices: Your Ultimate Guide
Listen up, folks. If you're reading this, chances are you're either diving into the world of IoT or you've already dipped your toes in and now want to tighten the screws on security and control. SSH control for IoT devices is no longer a luxury—it’s a necessity. Think about it: every smart device in your home or office is like a little door. Now, imagine leaving those doors wide open. Not so smart, right? That's where SSH steps in, acting as your digital locksmith, ensuring only the right keys can unlock those doors. So, buckle up, because we're about to deep-dive into everything SSH for IoT.
SSH, or Secure Shell, is basically the superhero of remote access. It’s the tech that lets you control your IoT devices from afar, all while keeping everything secure. Whether you're tweaking settings on a smart thermostat or monitoring a security camera, SSH has got your back. But here's the kicker—it's not just about convenience; it's about safeguarding your digital kingdom. Without SSH, your IoT setup could be a sitting duck for hackers.
Now, don't get me wrong—SSH isn't some magical spell that instantly makes everything hacker-proof. It takes knowledge, the right tools, and a bit of elbow grease to set it up properly. But once you've got it running, you'll wonder how you ever managed without it. So, whether you're a tech enthusiast or just someone who wants to keep their smart home safe, this guide is your ticket to mastering SSH control for IoT devices.
Read also:Aisha Sofey Leaks Unveiling The Truth Behind The Controversy
What is SSH Control and Why Does it Matter for IoT?
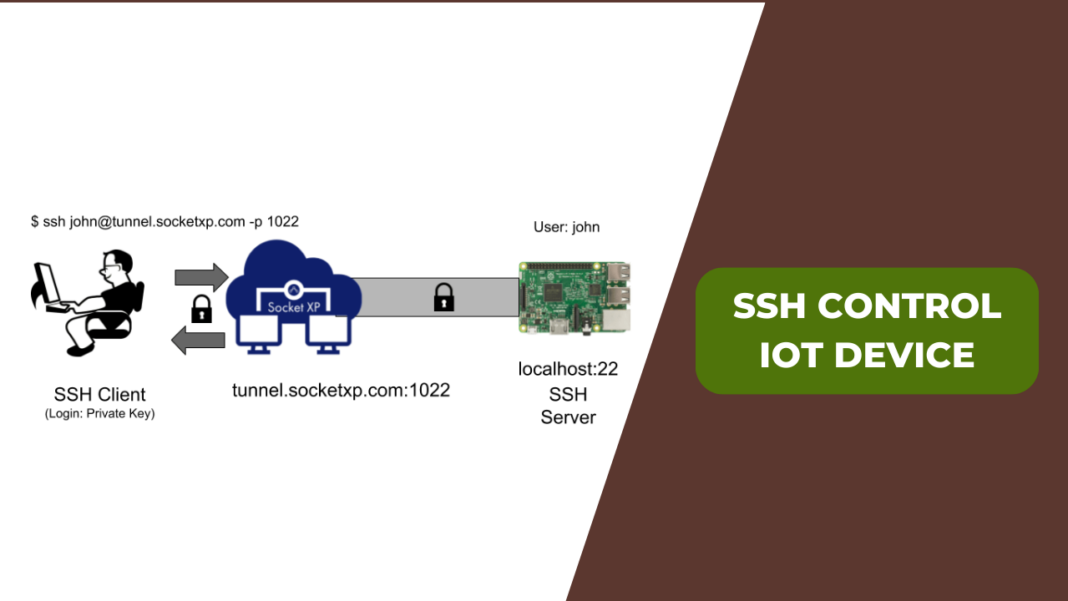
SSH control is like the VIP pass to your IoT world. It's the method that allows you to remotely connect to your devices over a secure channel. Imagine you're miles away from home, but you need to check if your smart lock is functioning properly. With SSH, you can log in, diagnose, and fix the issue without even leaving your couch—or wherever you might be. That's power, my friend.
But why is it so crucial for IoT? Well, think about the sheer number of devices we're talking about here. From smart bulbs to industrial sensors, each one is a potential entry point for cyber threats. SSH encrypts your communication, making it way harder for bad actors to snoop around or take control of your devices. It's not just about protecting your data; it's about maintaining the integrity of your entire IoT ecosystem.
Here's a quick rundown of why SSH is a game-changer:
- Secure Communication: SSH encrypts your data, keeping it safe from prying eyes.
- Remote Access: You can manage your IoT devices from anywhere in the world.
- Authentication: SSH ensures only authorized users can access your devices.
- Reliability: Once set up correctly, SSH provides stable and secure connections.
How SSH Works: A Simple Breakdown
Let's break it down into bite-sized chunks. SSH operates on a client-server model. Here's how it goes: you (the client) send a request to log into an IoT device (the server). The server checks your credentials and, if they're legit, grants you access. But here's the kicker—everything you send back and forth is encrypted, so even if someone intercepts your data, they won't be able to make sense of it.
SSH uses something called public-key cryptography. Think of it like a lockbox. You have a public key, which is like the lock, and a private key, which is the key that unlocks it. When you want to connect to a device, you send your public key. The device uses it to lock things up, and only your private key can unlock it. Pretty cool, huh?
Setting Up SSH for Your IoT Devices
Alright, let's get our hands dirty. Setting up SSH for your IoT devices isn't rocket science, but it does require a bit of patience and attention to detail. First things first, you'll need to ensure your devices support SSH. Most modern IoT devices come with SSH pre-installed, but if yours doesn't, don't panic—there are usually workarounds.
Read also:Schoolboy 9 The Rising Star Shaping The Future Of Music
Once you've confirmed SSH compatibility, here's what you need to do:
- Enable SSH: Head over to your device's settings and turn on SSH. Some devices might require you to install additional software or firmware updates.
- Generate Keys: Use a tool like PuTTY or OpenSSH to generate your public and private keys. This is the lock and key we talked about earlier.
- Set Up Authentication: Copy your public key to the device's authorized_keys file. This tells the device that you're a trusted user.
- Test the Connection: Use an SSH client to connect to your device. If everything's set up correctly, you should be able to log in without entering a password.
Tips for a Smooth Setup
Here are a few pro tips to make your SSH setup a breeze:
- Use Strong Passwords: Even though SSH uses keys, it's always good practice to have strong passwords as a backup.
- Regularly Update Firmware: Keeping your devices updated helps patch any security vulnerabilities.
- Monitor Connections: Keep an eye on who's accessing your devices. If you notice any suspicious activity, change your keys immediately.
Top SSH Clients for IoT Control
Not all SSH clients are created equal. Depending on your platform and preferences, you'll want to choose the right tool for the job. Here are some of the top SSH clients for controlling IoT devices:
1. PuTTY
PuTTY is a classic choice for Windows users. It's free, lightweight, and super easy to use. Plus, it supports a variety of protocols, including SSH. If you're just starting out, PuTTY is a great place to begin.
2. OpenSSH
OpenSSH is the go-to for Linux and macOS users. It's built into most Unix-based systems, so you don't even need to download anything. Just fire up your terminal and start connecting.
3. Termius
For those who want a more modern interface, Termius is a fantastic option. It's available on both desktop and mobile platforms, making it perfect for on-the-go IoT management.
Best Practices for SSH Control in IoT
Now that you've got SSH up and running, let's talk about best practices to keep your setup secure and efficient. Here are a few golden rules to live by:
- Disable Password Authentication: Stick to key-based authentication to eliminate the risk of brute-force attacks.
- Use Strong Keys: Longer keys are harder to crack, so opt for 2048-bit or higher RSA keys.
- Limit User Access: Only grant SSH access to users who absolutely need it.
- Monitor Logs: Regularly check your device logs for any unauthorized access attempts.
Common SSH Issues and How to Fix Them
Even the best-laid plans can hit a snag. Here are some common SSH issues you might encounter and how to fix them:
1. Connection Refused
This usually happens when the SSH service isn't running on the device. Double-check that SSH is enabled and restart the service if necessary.
2. Permission Denied
This often means there's an issue with your keys. Make sure your public key is correctly added to the authorized_keys file and that your private key is in the right location.
3. Timeout Errors
Timeouts can occur if there's a network issue or if the device is overloaded. Try restarting your router or the device itself.
SSH Control in Industrial IoT
SSH isn't just for home users—it's a cornerstone of industrial IoT as well. In industries like manufacturing, healthcare, and logistics, SSH ensures that critical systems remain secure and accessible. Imagine a factory where every machine is connected to a central control system. SSH allows engineers to remotely monitor and manage these machines, reducing downtime and increasing efficiency.
Case Study: Smart Manufacturing
A real-world example of SSH in action is in smart manufacturing plants. Companies like Siemens and GE use SSH to control everything from robotics to assembly lines. By leveraging SSH, they can perform maintenance, update software, and troubleshoot issues without ever setting foot on the factory floor.
Future Trends in SSH and IoT
The world of IoT is evolving rapidly, and SSH is evolving with it. One of the biggest trends we're seeing is the rise of quantum-resistant encryption. As quantum computing becomes more mainstream, traditional encryption methods might become obsolete. SSH developers are already working on solutions to ensure that our connections remain secure in the quantum age.
Quantum-Resistant SSH
Quantum-resistant SSH algorithms are designed to withstand attacks from quantum computers. While this technology is still in its infancy, it's something to keep an eye on if you're planning for the long term.
Conclusion: Take Control of Your IoT World
There you have it, folks—a comprehensive guide to mastering SSH control for IoT devices. From setting up SSH to troubleshooting common issues, we've covered it all. Remember, SSH isn't just about convenience—it's about security. By taking control of your IoT devices with SSH, you're not only protecting your data but also ensuring the smooth operation of your smart ecosystem.
So, what are you waiting for? Dive in, experiment, and take your IoT setup to the next level. And don't forget to share this article with your fellow tech enthusiasts. Together, we can build a safer, smarter future—one SSH connection at a time.
Table of Contents
- What is SSH Control and Why Does it Matter for IoT?
- How SSH Works: A Simple Breakdown
- Setting Up SSH for Your IoT Devices
- Top SSH Clients for IoT Control
- Best Practices for SSH Control in IoT
- Common SSH Issues and How to Fix Them
- SSH Control in Industrial IoT
- Future Trends in SSH and IoT
- Quantum-Resistant SSH
- Conclusion: Take Control of Your IoT World
Article Recommendations