Mastering IoT Device Monitoring Behind A Firewall With AWS: The Ultimate Guide
Hey there, tech enthusiasts and cloud wizards! If you're diving headfirst into the world of IoT (Internet of Things) and you're scratching your head over how to monitor IoT devices behind a firewall using AWS, you're in the right place. Today, we’re going to break down the ins and outs of this critical setup, ensuring your devices stay secure, efficient, and monitored like a hawk. So buckle up, because we’re about to demystify this complex but crucial aspect of modern tech infrastructure.
Let’s face it—IoT devices are everywhere. From smart homes to industrial automation, these little wonders are revolutionizing the way we interact with technology. But here's the catch: securing them while ensuring seamless monitoring is no small feat, especially when firewalls come into play. AWS offers some seriously powerful tools to help you tackle this challenge, and we’re here to walk you through every step.
By the end of this guide, you’ll not only understand how to set up monitoring for IoT devices behind a firewall but also gain insights into best practices, tools, and strategies that make your setup rock-solid. Ready to dive in? Let’s go!
Read also:Schoolboy 9 The Rising Star Shaping The Future Of Music
Table of Contents
- What is IoT Device Monitoring?
- Why Firewall Matters in IoT Monitoring
- AWS IoT Core: The Backbone of Your Setup
- Example of IoT Device Monitoring Behind a Firewall with AWS
- Tools and Techniques for Effective Monitoring
- Security Best Practices for IoT Devices
- Scaling Your IoT Monitoring Solution
- Troubleshooting Common Issues
- Real-World Use Cases
- Conclusion: Taking Your IoT Game to the Next Level
What is IoT Device Monitoring?
IoT device monitoring refers to the process of tracking and analyzing the performance, health, and security of IoT devices in real time. Think of it as the eyes and ears of your IoT ecosystem, keeping tabs on everything from device connectivity to data transmission and beyond. And here’s the kicker—it’s not just about monitoring; it’s about proactive problem-solving. By keeping a close eye on your devices, you can catch issues before they spiral out of control.
Why Monitoring is Crucial
Here’s the deal: IoT devices generate tons of data, and without proper monitoring, that data can become overwhelming—or worse, useless. Effective monitoring ensures that:
- Data is transmitted securely and efficiently.
- Devices remain in optimal working condition.
- Potential security threats are identified and mitigated promptly.
And let’s not forget—when you’ve got a firewall in the mix, things get a bit more complicated. But don’t worry, we’ve got you covered!
Why Firewall Matters in IoT Monitoring
Firewalls are like the bouncers at a club—they control who gets in and who stays out. In the context of IoT, firewalls play a critical role in securing your devices from unauthorized access. However, they can also create challenges when it comes to monitoring. If your firewall isn’t configured correctly, it could block the very data you need to monitor your IoT devices effectively.
Key Challenges
Some of the common hurdles you might face include:
- Restricted outbound connections.
- Port blocking that prevents data transmission.
- Complex rule configurations that require a deep understanding of both firewalls and IoT protocols.
But fear not! AWS has some killer solutions to help you navigate these challenges. Let’s dive into the heart of the matter—AWS IoT Core.
Read also:Alina Rose Naked Unveiling The Truth Behind The Sensation
AWS IoT Core: The Backbone of Your Setup
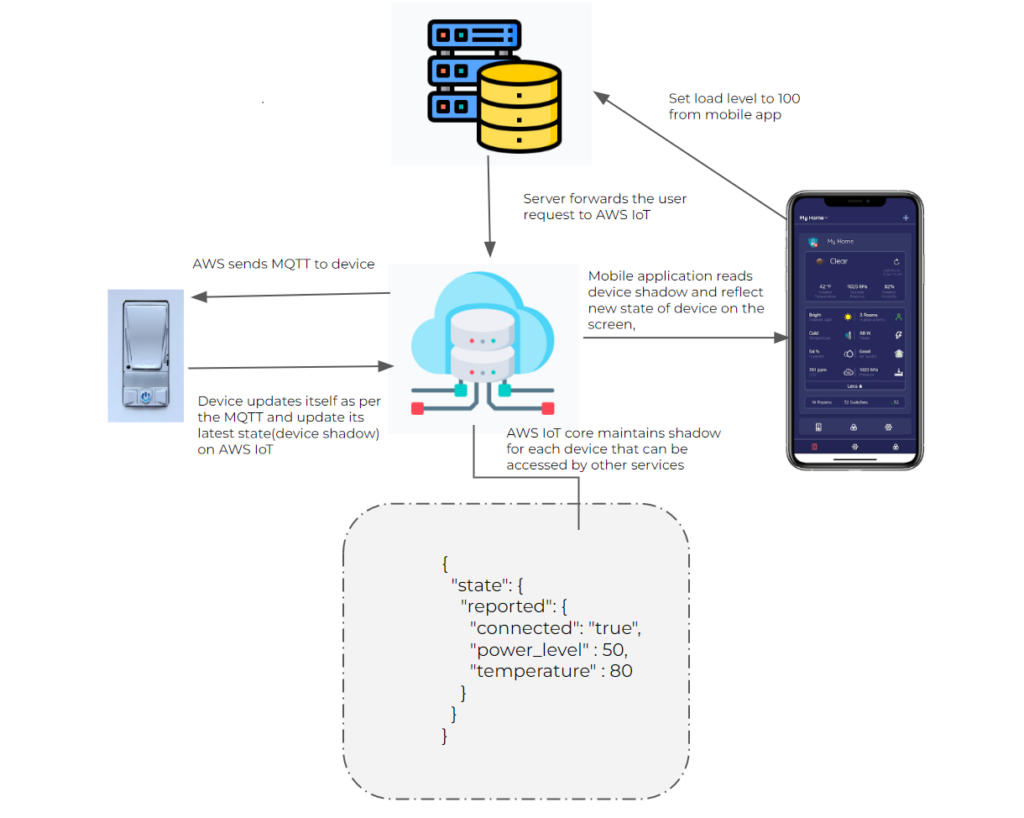
AWS IoT Core is like the Swiss Army knife of IoT solutions. It’s designed to connect, manage, and monitor billions of IoT devices securely and efficiently. With features like MQTT support, device shadows, and robust security protocols, AWS IoT Core makes it easier than ever to monitor IoT devices, even behind a firewall.
Key Features
Here are some of the standout features of AWS IoT Core:
- Messaging Protocols: Supports MQTT, HTTP, and WebSockets for flexible communication.
- Device Shadows: Enables you to sync device states even when they’re offline.
- Security: Offers end-to-end encryption and authentication to keep your data safe.
Now that we’ve covered the basics, let’s move on to a practical example of setting up IoT device monitoring behind a firewall using AWS.
Example of IoT Device Monitoring Behind a Firewall with AWS
Alright, let’s get hands-on. Here’s a step-by-step example of how you can set up monitoring for IoT devices behind a firewall using AWS IoT Core:
Step 1: Set Up Your AWS IoT Core
First things first—create an AWS account if you haven’t already. Then, navigate to the AWS IoT Core console and set up your IoT Core environment. This includes:
- Creating a thing (a virtual representation of your IoT device).
- Configuring policies and certificates for secure communication.
Step 2: Configure Your Firewall
Next, you’ll need to configure your firewall to allow outbound connections to AWS IoT Core. This typically involves:
- Opening specific ports (e.g., 8883 for MQTT).
- Allowing traffic to AWS IoT Core endpoints.
Step 3: Deploy Your IoT Device
Once your firewall is set up, deploy your IoT device and connect it to AWS IoT Core. Use the AWS SDK or CLI to send and receive messages, and start monitoring your device in real time.
Tools and Techniques for Effective Monitoring
Now that you’ve got the basics down, let’s talk about the tools and techniques that can take your monitoring game to the next level. Here are a few essentials:
CloudWatch
AWS CloudWatch is your go-to tool for monitoring metrics and logs. It allows you to track device performance, detect anomalies, and set up alerts for critical events.
IoT Analytics
For deeper insights, AWS IoT Analytics provides advanced data processing and analysis capabilities. Use it to uncover trends, identify patterns, and make data-driven decisions.
Security Best Practices for IoT Devices
Security should always be at the forefront of your IoT strategy. Here are some best practices to keep your devices safe:
- Use strong authentication and encryption protocols.
- Regularly update firmware and software to patch vulnerabilities.
- Implement network segmentation to isolate IoT devices from other systems.
By following these practices, you can significantly reduce the risk of security breaches and ensure your devices remain protected.
Scaling Your IoT Monitoring Solution
As your IoT ecosystem grows, so too should your monitoring solution. AWS offers scalable infrastructure that can handle thousands—or even millions—of devices. Whether you’re expanding your fleet or adding new features, AWS has the tools to keep up with your demands.
Auto Scaling
Use AWS Auto Scaling to dynamically adjust resources based on demand, ensuring optimal performance and cost efficiency.
Troubleshooting Common Issues
Even the best-laid plans can hit a snag. Here are some common issues you might encounter and how to fix them:
- Connection Issues: Check firewall settings and ensure all required ports are open.
- Data Loss: Verify that your devices are sending data correctly and that AWS IoT Core is receiving it.
- Performance Bottlenecks: Use CloudWatch to identify and resolve bottlenecks in your system.
Real-World Use Cases
To give you a better idea of how this works in practice, here are a couple of real-world use cases:
Smart Manufacturing
In a smart factory, IoT devices are used to monitor machinery and optimize production processes. By setting up monitoring behind a firewall, manufacturers can ensure secure and reliable data transmission while maintaining compliance with industry standards.
Healthcare
In healthcare, IoT devices are used to monitor patient health in real time. By leveraging AWS IoT Core and secure firewall configurations, healthcare providers can ensure patient data remains private and secure.
Conclusion: Taking Your IoT Game to the Next Level
And there you have it—a comprehensive guide to monitoring IoT devices behind a firewall using AWS. By following the steps and best practices outlined in this article, you can create a robust, scalable, and secure IoT monitoring solution that meets the demands of today’s tech-driven world.
So what are you waiting for? Start implementing these strategies today and take your IoT game to the next level. And don’t forget to share your thoughts, questions, or feedback in the comments below. We’d love to hear from you!
Article Recommendations