How To Use RemoteIoT Behind Firewall On Mac Without Hassle
Are you tired of being stuck behind a firewall while trying to access RemoteIoT on your Mac? Let’s face it, firewalls can be a real pain, but they’re here to protect us—whether we like it or not. But what if you need to use RemoteIoT for work or personal projects? Don’t worry, I’ve got your back. In this guide, we’ll explore how to use RemoteIoT behind a firewall on your Mac without breaking a sweat. Whether you’re a tech enthusiast or just someone looking to get things done, this article has got all the answers you need.
Using RemoteIoT behind a firewall isn’t as complicated as it sounds. With the right tools and techniques, you can bypass restrictions and connect seamlessly. This guide will walk you through every step, from understanding firewalls to configuring your Mac for RemoteIoT access. So, if you’re ready to take control of your IoT experience, let’s dive right in!
Before we begin, let’s address the elephant in the room. Firewalls are designed to keep unwanted traffic out, but they can also block legitimate connections. The good news is that there are ways to work around these restrictions without compromising your security. By the end of this article, you’ll have a solid understanding of how to use RemoteIoT behind a firewall on your Mac without any issues. Let’s get started!
Read also:Seven Sirius Benjamin A Rising Star In The Entertainment World
Understanding Firewalls and Their Role in IoT
First things first, let’s break down what firewalls actually do. A firewall is essentially a security system that monitors and controls incoming and outgoing network traffic. It acts as a gatekeeper, allowing or denying access based on predefined rules. When it comes to IoT devices, firewalls can sometimes block connections, making it tricky to use tools like RemoteIoT.
But why does this happen? Well, firewalls are designed to protect your network from unauthorized access. They analyze data packets and decide whether to allow them through or block them. While this is great for security, it can also create roadblocks for legitimate applications like RemoteIoT. Understanding how firewalls work is the first step toward overcoming these challenges.
Types of Firewalls and Their Impact on RemoteIoT
Not all firewalls are created equal. There are different types of firewalls, each with its own strengths and weaknesses. Here’s a quick rundown:
- Network Firewalls: These are hardware-based and typically used in corporate environments. They control traffic at the network level.
- Application Firewalls: These focus on specific applications and protocols. They’re great for fine-tuning access control.
- Host-Based Firewalls: These are software-based and installed on individual devices. macOS comes with its own built-in firewall, which we’ll discuss later.
Each type of firewall can impact your ability to use RemoteIoT differently. Knowing which one you’re dealing with is key to troubleshooting connection issues.
Why Use RemoteIoT Behind a Firewall?
Now that we’ve covered the basics of firewalls, let’s talk about why you’d want to use RemoteIoT behind one. RemoteIoT is a powerful tool for managing and monitoring IoT devices from anywhere. Whether you’re a developer testing new hardware or a homeowner managing smart devices, RemoteIoT can make your life easier.
But what happens when a firewall gets in the way? Instead of giving up, you can configure your system to work around these restrictions. By doing so, you ensure that your IoT setup remains functional and secure. Plus, you’ll gain valuable knowledge about network security and troubleshooting.
Read also:Trippie Redd Leaked Tapes The Untold Story Behind The Hype
Benefits of Using RemoteIoT on a Mac
Mac users have a unique advantage when it comes to IoT management. macOS offers a robust set of tools and features that make it easier to configure and use RemoteIoT. Here are some benefits:
- Native Support: macOS provides built-in support for many IoT protocols, making it easier to integrate with RemoteIoT.
- Security Features: The macOS firewall is highly customizable, allowing you to fine-tune your settings for optimal performance.
- User-Friendly Interface: With its intuitive design, macOS makes it simple to manage complex IoT setups.
These advantages make macOS an ideal platform for using RemoteIoT behind a firewall.
Step-by-Step Guide to Using RemoteIoT Behind a Firewall on Mac
Ready to get started? Follow these steps to configure RemoteIoT on your Mac while working behind a firewall:
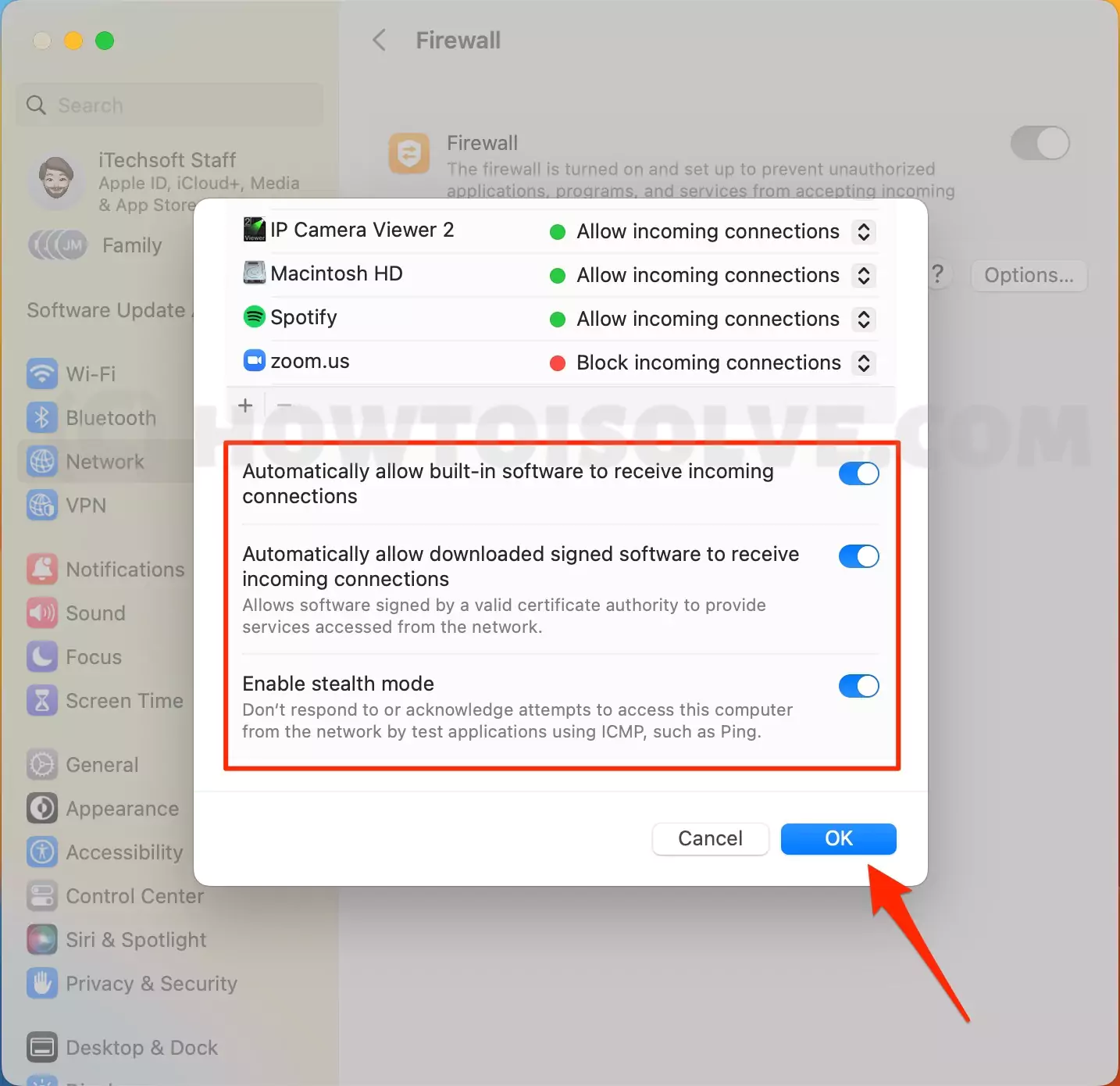
Step 1: Check Your Firewall Settings
The first step is to check your firewall settings. macOS comes with a built-in firewall that you can access through System Preferences. Here’s how:
- Open System Preferences on your Mac.
- Click on Security & Privacy.
- Go to the Firewall tab.
- Click the lock icon and enter your password to make changes.
- Turn on the firewall if it’s not already enabled.
Once your firewall is active, you can start configuring it for RemoteIoT.
Step 2: Allow RemoteIoT Through the Firewall
To use RemoteIoT behind a firewall, you need to allow it through the firewall’s rules. Here’s how:
- Go back to the Firewall tab in System Preferences.
- Click on Firewall Options.
- Add RemoteIoT to the list of allowed applications.
- Make sure to check the box for Allow incoming connections.
By allowing RemoteIoT through the firewall, you ensure that it can communicate with your IoT devices without interruptions.
Step 3: Configure Port Forwarding
Port forwarding is another crucial step when using RemoteIoT behind a firewall. This process involves mapping specific ports to your Mac’s IP address, allowing RemoteIoT to bypass firewall restrictions. Here’s how to do it:
- Log in to your router’s admin interface.
- Find the Port Forwarding section.
- Create a new rule and specify the port number used by RemoteIoT.
- Set the internal IP address to your Mac’s address.
With port forwarding configured, your Mac will be able to receive incoming connections from RemoteIoT.
Troubleshooting Common Issues
Even with the best setup, things can go wrong. Here are some common issues you might encounter when using RemoteIoT behind a firewall and how to fix them:
Issue 1: Connection Timeout
If you’re experiencing connection timeouts, it could be due to incorrect port settings. Double-check that the port number in RemoteIoT matches the one configured in your router.
Issue 2: Blocked Connections
Blocked connections are often caused by overly restrictive firewall rules. Review your firewall settings and ensure that RemoteIoT is explicitly allowed.
Issue 3: Slow Performance
Sometimes, firewalls can slow down network traffic. If you notice sluggish performance, try disabling unnecessary firewall rules or upgrading your router firmware.
Advanced Techniques for Bypassing Firewalls
For those who want to take things to the next level, here are some advanced techniques for bypassing firewalls:
Using a Proxy Server
A proxy server acts as an intermediary between your Mac and the internet. By routing your traffic through a proxy, you can bypass firewall restrictions. Popular proxy services include:
- Squid
- Privoxy
- CCProxy
Implementing SSH Tunneling
SSH tunneling is another effective way to bypass firewalls. It involves creating a secure connection between your Mac and a remote server, allowing RemoteIoT to communicate freely. Tools like PuTTY and OpenSSH can help you set up SSH tunnels with ease.
Best Practices for Secure IoT Management
While it’s important to bypass firewalls when necessary, security should always be a top priority. Here are some best practices for managing IoT devices securely:
- Regularly Update Firmware: Keep your IoT devices up to date with the latest security patches.
- Use Strong Passwords: Avoid using default passwords for your devices.
- Monitor Network Activity: Keep an eye on your network for any suspicious activity.
By following these guidelines, you can enjoy the benefits of RemoteIoT while minimizing risks.
Conclusion
In conclusion, using RemoteIoT behind a firewall on your Mac doesn’t have to be a daunting task. With the right tools and techniques, you can bypass restrictions and manage your IoT devices with ease. From configuring firewall settings to implementing advanced bypass methods, this guide has covered everything you need to know.
So, what are you waiting for? Take action today and start exploring the full potential of RemoteIoT. Don’t forget to share your thoughts in the comments below and check out our other articles for more tips and tricks. Happy networking!
Table of Contents
Article Recommendations