How To Remote Connect IoT Device Behind Firewall Example AWS
So here's the deal, you're probably scratching your head wondering how to remote connect IoT devices behind a firewall using AWS. It’s not as complicated as it sounds, but yeah, it does take some finesse. Picture this: you’ve got all these cool gadgets and gizmos that need to talk to each other, but your firewall is like a bouncer at a super exclusive club—only letting in the VIPs. That’s where AWS comes in, acting like a golden ticket to bypass those pesky restrictions. Let’s dive into how you can make this magic happen without losing your sanity.
Now, if you're reading this, chances are you're already knee-deep in the world of IoT. But just in case you're new to the scene, let me break it down for ya. IoT—or Internet of Things—is basically a network of devices that can communicate with each other over the internet. Sounds awesome, right? But when you throw a firewall into the mix, things can get a little tricky. That’s why we’re gonna walk you through an example using AWS to ensure your IoT devices stay connected no matter what.
Before we get started, it’s important to note that this isn’t just about connecting devices. It’s about doing it securely, efficiently, and in a way that won’t make your IT team pull their hair out. So buckle up, because we’re about to take you on a journey through the wild world of remote IoT connections behind firewalls with AWS. Ready? Let’s go!
Read also:Alina Rose Naked Unveiling The Truth Behind The Sensation
Understanding the Basics of Remote IoT Connections
Alrighty, let’s kick things off by getting our basics straight. When we talk about remote connecting IoT devices behind a firewall, we’re essentially looking at how to enable communication between devices without compromising security. Think of it like setting up a secret handshake that only the right devices can perform. AWS offers a variety of tools and services that make this possible, and we’ll be exploring some of them in detail.
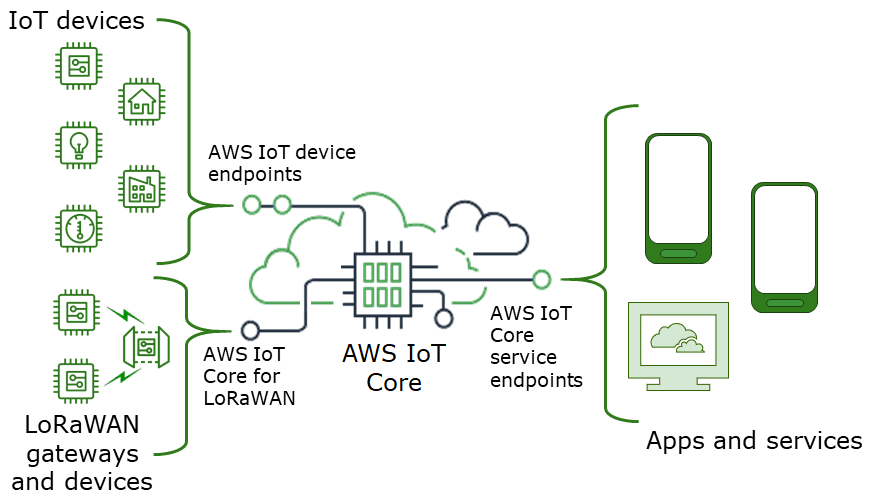
One of the key players in this game is AWS IoT Core. This bad boy allows you to securely interact with IoT devices no matter where they’re located. It handles all the heavy lifting, from authentication to data encryption, so you don’t have to sweat the small stuff. Plus, it integrates seamlessly with other AWS services, giving you even more flexibility and power.
Now, let’s talk about why this is important. In today’s connected world, businesses rely heavily on IoT devices to gather data, automate processes, and improve efficiency. But without a secure and reliable way to connect these devices, all that potential goes to waste. That’s where our trusty friend AWS comes in, providing the tools you need to make it happen.
Setting Up AWS IoT Core for Remote Connections
Alright, now that we’ve got the basics down, let’s move on to the nitty-gritty. Setting up AWS IoT Core for remote connections is a crucial step in the process. First things first, you’ll need to create an AWS account if you don’t already have one. Don’t worry, it’s pretty straightforward. Once you’re logged in, head over to the AWS Management Console and navigate to the IoT Core service.
From there, you’ll want to set up your IoT registry. This is where you’ll register all your devices and manage their settings. Think of it like a guest list for your IoT party. You can also create policies to define what each device is allowed to do, ensuring everything stays nice and secure.
Another important step is setting up your certificates. These are like IDs for your devices, proving they’re who they say they are. AWS IoT Core makes it easy to generate and manage these certificates, so you don’t have to worry about losing track of them. Just remember to keep them safe and sound.
Read also:Timothy Hawking The Untold Story Of Stephen Hawkings Eldest Son
Creating a Secure Communication Channel
Now that your devices are all set up in the registry, it’s time to create a secure communication channel. This is where AWS IoT Core really shines. It uses MQTT—a lightweight messaging protocol designed specifically for IoT devices—to facilitate communication between devices. MQTT is super efficient, making it perfect for low-bandwidth environments.
To ensure everything stays secure, AWS IoT Core uses TLS (Transport Layer Security) to encrypt all data transmitted between devices. This means even if someone intercepts the data, they won’t be able to make sense of it without the proper credentials. Pretty neat, huh?
Additionally, you can set up rules to automatically process incoming data. For example, you could configure a rule to send temperature readings from a sensor to an S3 bucket for storage. This not only simplifies data management but also gives you more control over how your data is used.
Firewall Configuration for IoT Devices
Let’s talk about firewalls for a sec. Firewalls are like bouncers, but instead of keeping out unruly party guests, they keep out unwanted internet traffic. When you’re trying to connect IoT devices behind a firewall, you’ve got to make sure the firewall knows what’s allowed and what’s not.
One common approach is to configure your firewall to allow traffic only on specific ports. For example, AWS IoT Core uses port 8883 for MQTT communication. By opening this port on your firewall, you can ensure your devices can communicate without issue. Just be sure to lock down any other unnecessary ports to maintain security.
Another option is to use a proxy server. This acts as a middleman, allowing your devices to communicate with AWS IoT Core without directly exposing them to the internet. It’s like having a trusted friend relay messages for you, ensuring everything stays safe and secure.
Using AWS VPC for Enhanced Security
If you’re looking for an extra layer of security, consider using AWS Virtual Private Cloud (VPC). This allows you to create a private network within AWS, giving you more control over how your devices connect. You can set up subnets, security groups, and network access control lists to further restrict access.
For example, you could create a subnet specifically for your IoT devices, ensuring they’re isolated from other parts of your network. Then, you could configure security groups to only allow traffic from specific IP addresses, adding another layer of protection.
Using AWS VPC not only enhances security but also improves performance by reducing latency and increasing reliability. It’s a win-win situation.
Example of Remote Connecting IoT Devices
Alright, let’s walk through an example to see how all this comes together. Imagine you’ve got a temperature sensor in a remote location that needs to send data to a cloud database. Here’s how you’d set it up:
- Register the sensor in the AWS IoT registry.
- Create a policy allowing the sensor to publish data to a specific topic.
- Generate and install a certificate on the sensor.
- Configure the sensor to connect to AWS IoT Core using MQTT on port 8883.
- Set up a rule to forward the data to an S3 bucket for storage.
Once everything’s configured, your sensor will start sending data to the cloud automatically. You can then access this data from anywhere in the world, all without exposing your sensor to unnecessary risks.
Troubleshooting Common Issues
Of course, things don’t always go as planned. If you run into issues, here are a few common problems and how to fix them:
- Connection Refused: Check your firewall settings to ensure the correct ports are open.
- Authentication Failed: Verify your certificates are installed correctly and haven’t expired.
- Data Not Reaching S3: Double-check your rules configuration to ensure they’re set up properly.
Remember, troubleshooting is all about narrowing down the problem and addressing it step by step. Don’t get discouraged if things don’t work right away—it’s all part of the process.
Best Practices for Secure IoT Connections
Now that we’ve covered the basics and walked through an example, let’s talk about best practices for keeping your IoT connections secure. First and foremost, always use strong authentication and encryption. This means using certificates, passwords, and other security measures to ensure only authorized devices can connect.
Another important practice is regularly updating your devices and software. This helps patch any vulnerabilities and ensures you’re always running the latest and greatest. Think of it like giving your devices a regular tune-up to keep them running smoothly.
Finally, monitor your devices closely for any suspicious activity. AWS IoT Core makes this easy by providing detailed logs and metrics. By keeping an eye on things, you can quickly identify and address any potential issues before they become major problems.
Utilizing AWS CloudWatch for Monitoring
Speaking of monitoring, AWS CloudWatch is a powerful tool for keeping tabs on your IoT devices. It allows you to collect and track metrics, set alarms, and automate responses to changes in your data. For example, you could set up an alarm to notify you if a device stops sending data, allowing you to quickly investigate and resolve the issue.
CloudWatch also integrates with other AWS services, giving you even more flexibility and control. Whether you’re monitoring device performance or tracking data trends, CloudWatch has got you covered.
Future Trends in IoT and AWS
So where’s all this heading? Well, the future of IoT and AWS looks pretty bright. As more and more devices become connected, the demand for secure and efficient communication solutions will only increase. AWS is already at the forefront of this movement, constantly innovating and improving its offerings.
One exciting development is the rise of edge computing. This allows devices to process data locally, reducing latency and improving performance. AWS offers services like AWS Greengrass that make it easy to implement edge computing solutions, giving you even more options for optimizing your IoT setup.
Another trend to watch is the increasing use of AI and machine learning in IoT applications. By leveraging these technologies, businesses can gain deeper insights into their data and make more informed decisions. AWS provides a range of AI and ML services that integrate seamlessly with IoT, opening up endless possibilities.
Staying Ahead of the Curve
To stay ahead in the world of IoT, it’s important to keep learning and adapting. Follow industry news, attend conferences, and experiment with new technologies. AWS offers a wealth of resources to help you stay up to date, including documentation, training, and community forums.
By staying informed and proactive, you’ll be well-equipped to tackle whatever challenges come your way. And who knows? You might just discover the next big thing in IoT while you’re at it.
Conclusion: Taking Action
Well, there you have it—a comprehensive guide to remote connecting IoT devices behind firewalls using AWS. From understanding the basics to implementing best practices, we’ve covered everything you need to know to get started. Remember, the key to success is staying secure, efficient, and adaptable.
So what are you waiting for? Dive in, experiment, and see what you can create. And don’t forget to share your experiences and insights with the community. The more we learn from each other, the stronger we become. Now go forth and conquer the world of IoT!
Table of Contents
Article Recommendations